I received solstice greetings via snail-mail from fellow security engineers in Bigbank, guys I used to work with. Only, when ethical hackers send messages, they send them… securely.
The outer envelope was marked as registered mail. Inside:
- Security stickers, because, obviously
- A merry fir tree card
- …but you had to enable macros to get it to show
- Security envelope, properly sealed with a security seal
- Inside, an USB drive

USB teardown
The USB drive was named “nimda” (__<<admin - RTL override?) and contained insecurity.png.
~/tmp » ls -lh
total 867M
-rw-r--r-- 1 ando ando 867M dets 17 12:34 insecurity.png
~/tmp » stat insecurity.png
File: insecurity.png
Size: 908809605 Blocks: 1775032 IO Block: 4096 regular file
Device: fd00h/64768d Inode: 1447295 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ ando) Gid: ( 1000/ ando)
Access: 2018-12-20 18:28:02.900991000 +0200
Modify: 2018-12-17 12:34:24.000000000 +0200
Change: 2018-12-20 18:28:02.202816787 +0200
Birth: -
~/tmp » file insecurity.png
insecurity.png: PNG image data, 300 x 300, 8-bit colormap, non-interlaced
So, it is (actually) a 300x300px .PNG image. The obvious question though - WTF is up with the 867M file size? Interestingly, Nautilus had no problems displaying the thumbnail.
It’s my avatar.
Maybe the guys used PNG metadata to hide a hidden message or artificially enlarge the file size? Let’s inspect with
$ identify -verbose insecurity.png
Seems like not. What about hexdump, this should give an indication of what’s actually there…
$ hexdump -C insecurity.png -n 90000 | less
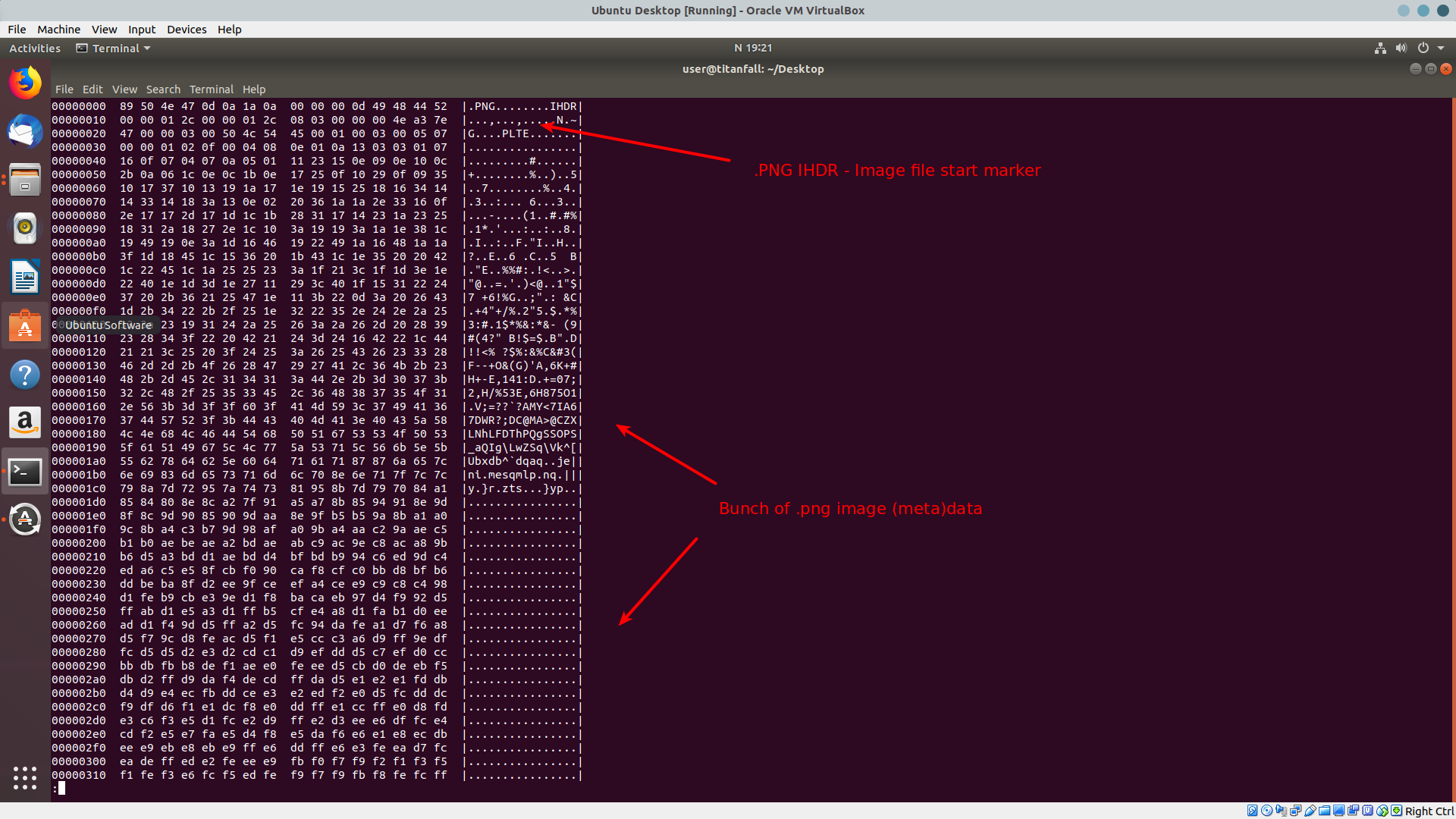
The file starts with a .png image, as expected. This is why Nautilus was able to render the thumbnail. However, scrolling down, we see that at one point not far into the file, the file ends with IEND marker, which according to .PNG specification, “marks the end of the PNG datastream”.
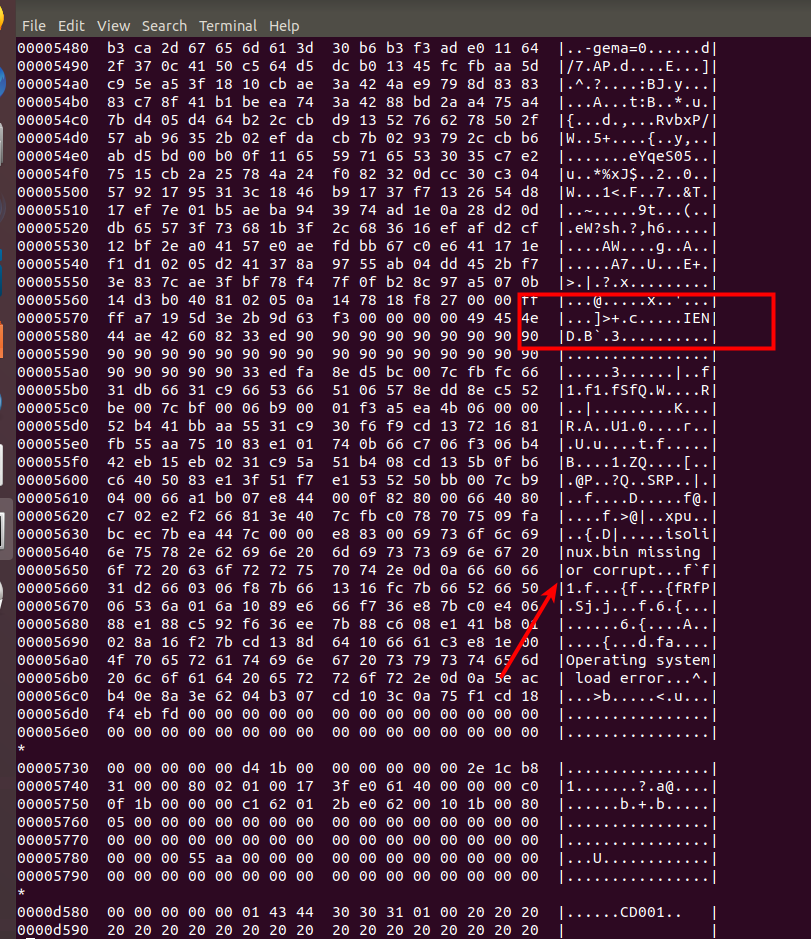
What follows makes it clear why the file was so large.
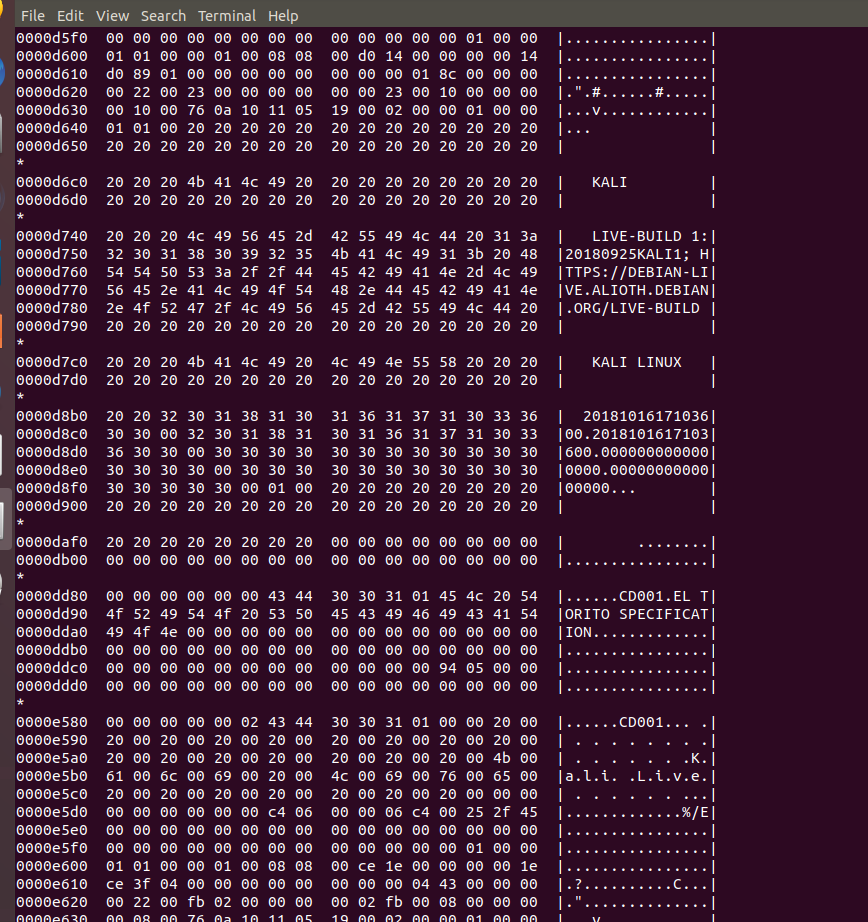
The guys have hidden the latest .iso of Kali Linux into the .PNG file.
Have you ever thought how to hide your hacking distros? An image* will do.
Card teardown
The printed-out card they sent had two sides: one Word document, directing the user to enable content, the other wishing merry Christmas.


Most people don’t know this, but whenever you print something with a color printer, the printer embeds tiny tracking fingerprints in the paper, in yellow color. You won’t be able to see it with a naked eye, but in case it’s ever needed, this marker will be able to identify from which printer a particular paper came from. This is how they were able to identify a whistleblower in NSA.
Let’s see if the markers (or any other hidden messages) are present in the card.
We’ll start by taking a high-resolution scan (best quality possible <600dpi) of the paper.
The resulting .PDF can be opened in Gimp.
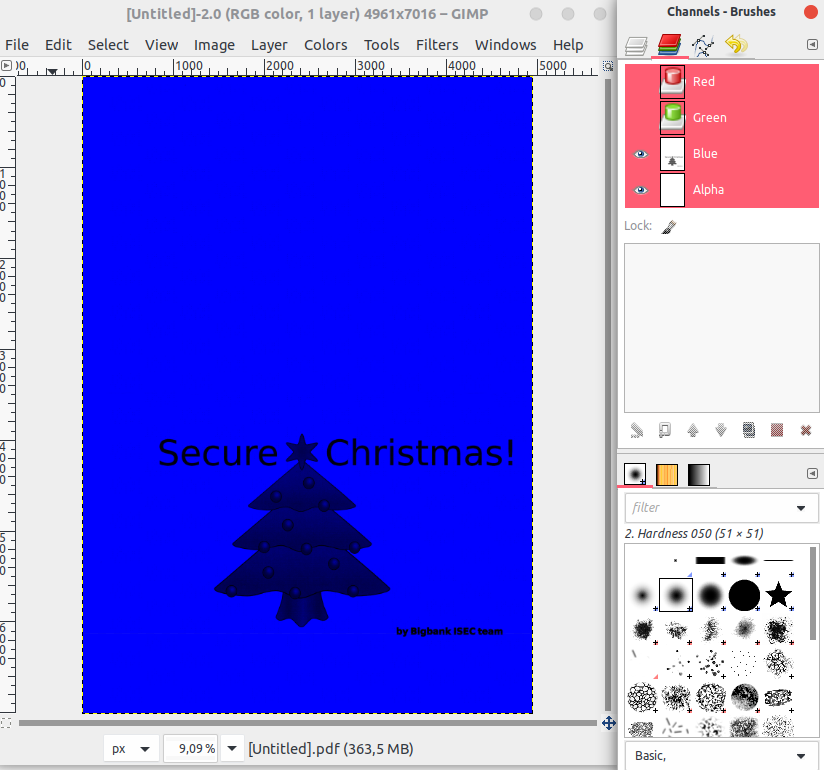
Using the color Channels dialog, we’ll hide the Red and Green color channels, leaving only the blue. And zoom in.

Looking closely, we can see tiny black dots with the same pattern, distributed across the page. Zooming in on one of them gives us the unique fingerprint of the printer in questions.

So, if you ever receive printouts with the same fingerprint, you know it came from their printer.
All-in-all, an excellent hackish solstice wish. Thanks, guys!
Bigbank Information Security Team (ISEC) is a blue team of hackers, who tries to keep the bank safe from exploitation and data breaches.